[2016-NEW!] Free 70-411 447q Exam Dumps With New Update Exam Questions And Answers (Question 271 – Question 300)
70-411 Braindumps, 70-411 Exam Dumps, 70-411 Exam Questions, 70-411 PDF Dumps, 70-411 Practice Tests, 70-411 Study Guide, 70-411 VCE Dumps, Microsoft Braindumps
100% Valid Dumps For 70-411 Exam Passing: PassLeader have been updated the 447q 70-411 exam dumps and added the new exam questions, in the newest version of 70-411 PDF dumps and 70-411 VCE dumps, you will get all the new updated 70-411 exam questions, which will help you 100% passing 70-411 exam, and you will get the free version of VCE simulator together with your 70-411 VCE dumps. Welcome to visit our website — passleader.com and get your 70-411 exam passed easily!
keywords: 70-411 exam,447q 70-411 exam dumps,447q 70-411 exam questions,70-411 pdf dumps,70-411 vce dumps,70-411 study guide,70-411 practice test,Administering Windows Server 2012 R2 Exam
P.S. Download Free 70-411 PDF Dumps and Preview PassLeader 70-411 VCE Dumps At The End Of This Post!!! (Ctrl+End)
QUESTION 271
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Desktop Session Host role service installed. The computer account of Server1 resides in an organizational unit (OU) named OU1. You create and link a Group Policy object (GPO) named GPO1 to OU1. GPO1 is configured as shown in the exhibit. (Click the Exhibit button.)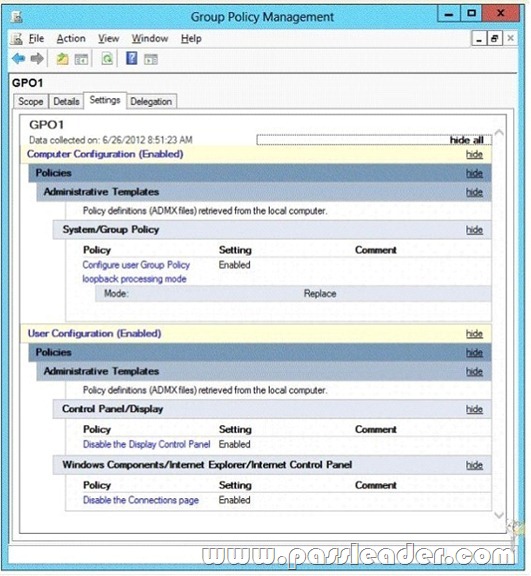
You need to prevent GPO1 from Applying to your user account when you log on to Server1. GPO1 must Apply to every other user who logs on to Server1. What should you configure?
A. WMI Filtering
B. Item-level Targeting
C. Block Inheritance
D. Security Filtering
Answer: D
QUESTION 272
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 is backed up daily. The domain has the Active Directory Recycle Bin enabled. During routine maintenance, you delete 500 inactive user accounts and 100 inactive groups. One of the deleted groups is named Group1. Some of the deleted user accounts are members of some of the deleted groups. For documentation purposes, you must provide a list of the members of Group1 before the group was deleted. You need to identify the names of the users who were members of Group1 prior to its deletion. You want to achieve this goal by using the minimum amount of administrative effort. What should you do first?
A. Mount the most recent Active Directory backup.
B. Perform an authoritative restore of Group1.
C. Use the Recycle Bin to restore Group1.
D. Reactivate the tombstone of Group1.
Answer: A
QUESTION 273
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Both servers run Windows Server 2012 R2. For Server2, you are configuring constrained delegation to a third-party service named Service1 on Server1. When you attempt to add Service1 from Server1 to the delegation setting of Server2, you discover that Service1 is not listed in the Available services list. You need to ensure that you can add Service1 for constrained delegation. What should you do first?
A. From the Services console, modify the properties of Service1
B. From ADSI Edit, create a serviceConnectionPoint (SCP) object
C. From a command prompt, run the setspn.exe command
D. From Active Directory Users and Computers, enable the Advanced Features option
Answer: A
QUESTION 274
You have a file server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed. Files created by users in the human resources department are assigned the Department classification property automatically. You are configuring a file management task named Task1 to remove user files that have not been accessed for 60 days or more. You need to ensure that Task1 only removes files that have a Department classification property of human resources. The solution must minimize administrative effort. What should you configure on Task1?
A. Create a custom action.
B. Configure a file screen.
C. Create a classification rule.
D. Create a condition.
Answer: D
QUESTION 275
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the Network Policy Server role service installed. An administrator creates a Network Policy Server (NPS) network policy named Policy1. You need to ensure that Policy1 applies to L2TP connections only. Which condition should you modify? To answer, select the appropriate object in the answer area.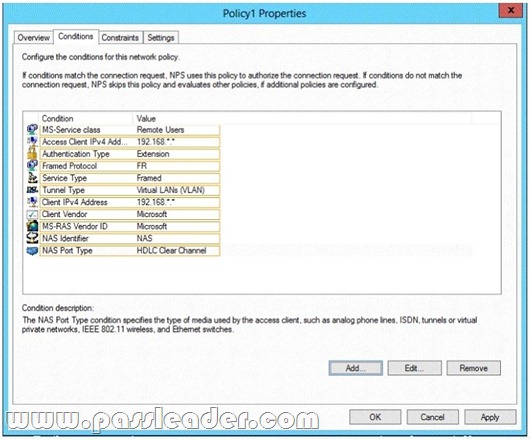
Answer: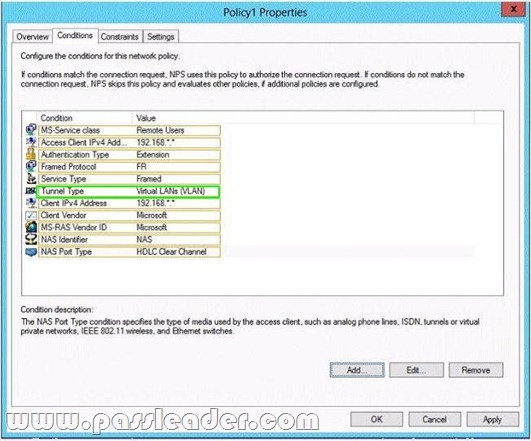
QUESTION 276
Your network contains two DNS servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 hosts a primary zone for contoso.com. Server2 hosts a secondary zone for contoso.com. You need to ensure that Server2 replicates changes to the contoso.com zone every five minutes. Which setting should you modify in the start of authority (SOA) record?
A. Retry interval
B. Minimum (default) TTL
C. Expires after
D. Refresh interval
Answer: D
QUESTION 277
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to OU1. You make a change to GPO1. You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort. Which tool should you use?
A. The Secedit command
B. The Set-AdComputer cmdlet
C. Active Directory Users and Computers
D. The Invoke-GpUpdate cmdlet
Answer: D
QUESTION 278
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two servers. The servers are configured as shown in the following table.
Server1 and Server2 host a load-balanced website named Web1. Web1 runs by using an application pool named WebApp1. WebApp1 uses a group Managed Service Account named gMSA1 as its identity. Domain users connect to Web1 by using either the name Web1.contoso.com or the alias myweb.contoso.com. You discover the following:
– When the users access Web1 by using Web1.contoso.com, they authenticate by using Kerberos.
– When the users access Web1 by using myweb.contoso.com, they authenticate by using NTLM.
You need to ensure that the users can authenticate by using Kerberos when they connect by using myweb.contoso.com. What should you do?
A. Run the Add-ADComputerServiceAccount cmdlet.
B. Modify the properties of the gMSA1 service account.
C. Modify the properties of the Web1 website.
D. Run the Install-ADServiceAccount cmdlet.
Answer: B
QUESTION 279
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. You create a central store for Group Policy. You receive a custom administrative template named Template1.admx. You need to ensure that the settings in Template1.admx appear in all new Group Policy objects (GPOs). What should you do?
A. Copy Template1.admx to \\Contoso.com\SYSVOL\Contoso.com\Policies\PolicyDefinitions\
B. From the Default Domain Controllers Policy, add Template1.admx to the Administrative Templates
C. Copy Template1.admx to \\Contoso.com\NETLOGON
D. From the Default Domain Policy, add Template1.admx to the Administrative Templates
Answer: A
QUESTION 280
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the Network Policy Server role service installed. An administrator creates a RADIUS client template named Template1. You create a RADIUS client named Client1 by using Template1. You need to modify the shared secret for Client1. What should you do first?
A. Clear Select an existing template for Client1
B. Set the Shared secret setting of Template1 to Manual.
C. Clear Enable this RADIUS client for Client1.
D. Configure the Advanced settings of Template1.
Answer: A
QUESTION 281
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. All of the DNS servers in both of the domains run Windows Server 2012 R2. The network contains two servers named Server1 and Server2. Server1 hosts an Active Directory-integrated zone for contoso.com. Server2 hosts an Active Directory-integrated zone for fabrikam.com. Server1 and Server2 connect to each other by using a WAN link. Client computers that connect to Server1 for name resolution cannot resolve names in fabrikam.com. You need to configure Server1 to resolve names in fabrikam.com. The solution must NOT require that changes be made to the fabrikam.com zone on Server2. What should you create?
A. a secondary zone
B. a stub zone
C. a trust anchor
D. a zone delegation
Answer: B
QUESTION 282
Your network contains an Active Directory domain named contoso.com. Network Access Protection (NAP) is deployed to the domain. You need to create NAP event trace log files on a client computer. What should you run?
A. Register-ObjectEvent
B. Register-EngineEvent
C. tracert
D. logman
Answer: D
QUESTION 283
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two servers. The servers are configured as shown in the following table.
Server1 and Server2 host a load-balanced website named Web1. Web1 runs by using an application pool named WebApp1. WebApp1 uses a group Managed Service Account named gMSA1 as its identity. Domain users connect to Web1 by using either the name Web1.contoso.com or the alias myweb.contoso.com. You discover the following:
– When the users access Web1 by using Web1.contoso.com, they authenticate by using Kerberos.
– When the users access Web1 by using myweb.contoso.com, they authenticate by using NTLM.
You need to ensure that the users can authenticate by using Kerberos when they connect by using myweb.contoso.com. What should you do?
A. Run the Set-ADServiceAccount cmdlet.
B. Run the New-ADServiceAccount cmdlet.
C. Modify the properties of the WebApp1 application pool.
D. Modify the properties of the Web1 website.
Answer: A
QUESTION 284
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012 R2. You have a Password Settings object (PSOs) named PSO1. You need to view the settings of PSO1. Which tool should you use?
A. Active Directory Administrative Center
B. Get-ADAccountResultantPasswordReplicationPolicy
C. Local Security Policy
D. Get-ADDomainControllerPasswordReplicationPolicy
Answer: A
QUESTION 285
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. Server1 has a share named Share1. When users without permission to Share1 attempt to access the share, they receive the Access Denied message as shown in the exhibit. (Click the Exhibit button.)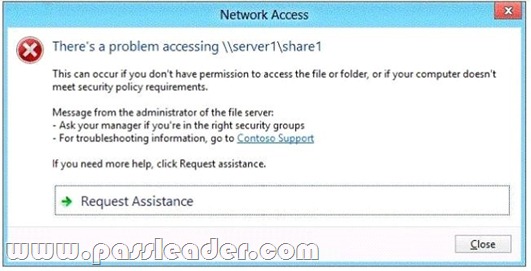
You deploy a new file server named Server2 that runs Windows Server 2012 R2. You need to configure Server2 to display the same custom Access Denied message as Server1. What should you install on Server2?
A. The Remote Assistance feature
B. The File Server Resource Manager role service
C. The Enhanced Storage feature
D. The Storage Services server role
Answer: B
QUESTION 286
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. Administrators use client computers that run Windows 8 to perform all management tasks. A central store is configured on a domain controller named DC1. You have a custom administrative template file named App1.admx. App1.admx contains application settings for an application named Appl. From a client computer named Computer1, you create a new Group Policy object (GPO) named GPO1. You discover that the application settings for App1 fail to appear in GPO1. You need to ensure that the App1 settings appear in all of the new GPOs that you create. What should you do?
A. Copy App1.admx to \\Contoso.com\SYSVOL\Contoso.com\Policies\PolicyDefinitions\
B. From the Default Domain Controllers Policy, add App1.admx to the Administrative Templates
C. From the Default Domain Policy, add App1.admx to the Administrative Templates
D. Copy App1.admx to \\Contoso.com\SYSVOL\Contoso.com\StarterGPOs
Answer: A
QUESTION 287
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. One of the domain controllers is named DC1. The DNS zone for the contoso.com zone is Active Directory-integrated and has the default settings. A server named Server1 is a DNS server that runs a UNIX-based operating system. You plan to use Server1 as a secondary DNS server for the contoso.com zone. You need to ensure that Server1 can host a secondary copy of the contoso.com zone. What should you do?
A. From Windows PowerShell, run the Set-DnsServerPrimaryZone cmdlet and specify the contoso.com zone as a target.
B. From DNS Manager, modify the Security settings of DC1.
C. From DNS Manager, modify the Zone Transfers settings of the contoso.com zone.
D. From DNS Manager, modify the Advanced settings of DC1.
Answer: C
QUESTION 288
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the Network Policy Server role service installed. You need to enable trace logging for Network Policy Server (NPS) on Server1. Which tool should you use?
A. the Network Policy Server console
B. the Server Manager console
C. the tracert.exe command
D. the netsh.exe command
Answer: D
QUESTION 289
Hotspot Question
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains two Active Directory sites named Site1 and Site2. You plan to deploy a read-only domain controller (RODC) named DC10 to Site2. You pre- create the DC10 domain controller account by using Active Directory Users and Computers. You need to identify which domain controller will be used for initial replication during the promotion of the RODC. Which tab should you use to identify the domain controller? To answer, select the appropriate tab in the answer area.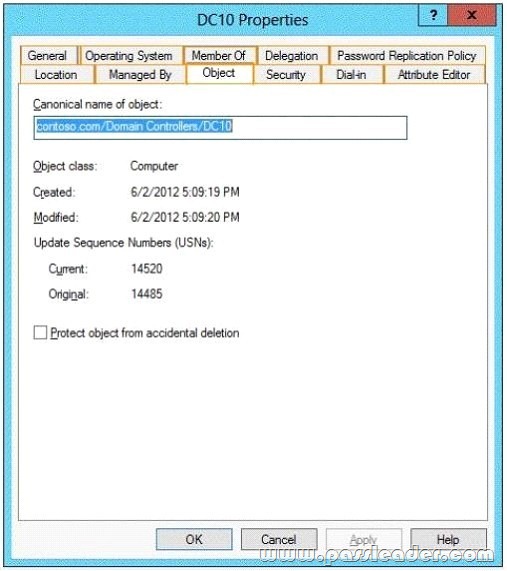
Answer:
QUESTION 290
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DNS Server server role installed. Server1 is configured to delete automatically the DNS records of client computers that are no longer on the network. A technician confirms that the DNS records are deleted automatically from the contoso.com zone. You discover that the contoso.com zone has many DNS records for servers that were on the network in the past, but have not connected to the network for a long time. You need to set the time stamp for all of the DNS records in the contoso.com zone. What should you do?
A. From DNS Manager, modify the Advanced settings from the properties of Server1
B. From Windows PowerShell, run the Set-DnsServerResourceRecordAging cmdlet
C. From DNS Manager, modify the Zone Aging/Scavenging Properties
D. From Windows PowerShell, run the Set-DnsServerZoneAging cmdlet
Answer: B
QUESTION 291
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. You enable and configure Routing and Remote Access (RRAS) on Server1. You create a user account named User1. You need to ensure that User1 can establish VPN connections to Server1. What should you do?
A. Modify the members of the Remote Management Users group.
B. Add a RADIUS client.
C. Modify the Dial-in setting of User1.
D. Create a connection request policy.
Answer: C
QUESTION 292
Your network contains an Active Directory domain named contoso.com. All user accounts reside in an organizational unit (OU) named OU1. All of the users in the marketing department are members of a group named Marketing. All of the users in the human resources department are members of a group named HR. You create a Group Policy object (GPO) named GPO1. You link GPO1 to OU1. You configure the Group Policy preferences of GPO1 to add two shortcuts named Link1 and Link2 to the desktop of each user. You need to ensure that Link1 only appears on the desktop of the users in Marketing and that Link2 only appears on the desktop of the users in HR. What should you configure?
A. Security Filtering
B. WMI Filtering
C. Group Policy Inheritance
D. Item-level targeting
Answer: D
QUESTION 293
Your network contains a single Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains 400 desktop computers that run Windows 8 and 10 desktop computers that run Windows XP Service Pack 3 (SP3). All new desktop computers that are added to the domain run Windows 8. All of the desktop computers are located in an organizational unit (OU) named OU1. You create a Group Policy object (GPO) named GPO1. GPO1 contains startup script settings. You link GPO1 to OU1. You need to ensure that GPO1 is applied only to computers that run Windows XP SP3. What should you do?
A. Create and link a WML filter to GPO1.
B. Run the Set-GPInheritance cmdlet and specify the -target parameter.
C. Run the Set-GPLink cmdlet and specify the -target parameter.
D. Modify the Security settings of OU1.
Answer: A
QUESTION 294
Your network contains an Active Directory domain named contoso.com. Network Policy Server (NPS) is deployed to the domain. You plan to deploy Network Access Protection (NAP). You need to configure the requirements that are validated on the NPS client computers. What should you do?
A. From the Network Policy Server console, configure a network policy.
B. From the Network Policy Server console, configure a health policy.
C. From the Network Policy Server console, configure a Windows Security Health Validator (WSHV) policy.
D. From a Group Policy object (GPO), configure the NAP Client Configuration security setting.
E. From a Group Policy object (GPO), configure the Network Access Protection Administrative Templates setting.
Answer: C
QUESTION 295
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server. The network contains two subnets named Subnet1 and Subnet2. Server1 has a DHCP scope for each subnet. You need to ensure that noncompliant computers on Subnet1 receive different network policies than noncompliant computers on Subnet2. Which two settings should you configure? (Each correct answer presents part of the solution. Choose two.)
A. The NAP-Capable Computers conditions
B. The NAS Port Type constraints
C. The Health Policies conditions
D. The MS-Service Class conditions
E. The Called Station ID constraints
Answer: CD
QUESTION 296
Your network contains an Active Directory domain named contoso.com. The functional level of the forest is Windows Server 2008 R2. Computer accounts for the marketing department are in an organizational unit (OU) named Departments\Marketing\Computers. User accounts for the marketing department are in an OU named Departments\Marketing\Users. All of the marketing user accounts are members of a global security group named MarketingUsers. All of the marketing computer accounts are members of a global security group named MarketingComputers. In the domain, you have Group Policy objects (GPOs) as shown in the exhibit. (Click the Exhibit button.)
You create two Password Settings objects named PSO1 and PSO2. PSO1 is applied to MarketingUsers. PSO2 is applied to MarketingComputers. The minimum password length is defined for each policy as shown in the following table.
You need to identify the minimum password length required for each marketing user. What should you identify?
A. 5
B. 6
C. 7
D. 10
E. 12
Answer: D
QUESTION 297
Your network contains an Active Directory domain named adatum.com. You need to audit changes to the files in the SYSVOL shares on all of the domain controllers. The solution must minimize the amount of SYSVOL replication traffic caused by the audit. Which two settings should you configure? (Each correct answer presents part of the solution. Choose two.)
A. Audit Policy\Audit system events
B. Advanced Audit Policy Configuration\DS Access
C. Advanced Audit Policy Configuration\Global Object Access Auditing
D. Audit Policy\Audit object access
E. Audit Policy\Audit directory service access
F. Advanced Audit Policy Configuration\Object Access
Answer: DF
QUESTION 298
Your network contains multiple Active Directory sites. You have a Distributed File System (DFS) namespace that has a folder target in each site. You discover that some client computers connect to DFS targets in other sites. You need to ensure that the client computers only connect to a DFS target in their respective site. What should you modify?
A. The properties of the Active Directory sites
B. The properties of the Active Directory site links
C. The delegation settings of the namespace
D. The referral settings of the namespace
Answer: D
QUESTION 299
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012. You have a Group Policy object (GPO) named GPO1 that contains several custom Administrative templates. You need to filter the GPO to display only settings that will be removed from the registry when the GPO falls out of scope. The solution must only display settings that are either enabled or disabled and that have a comment. How should you configure the filter? To answer, select the appropriate options below. Select three.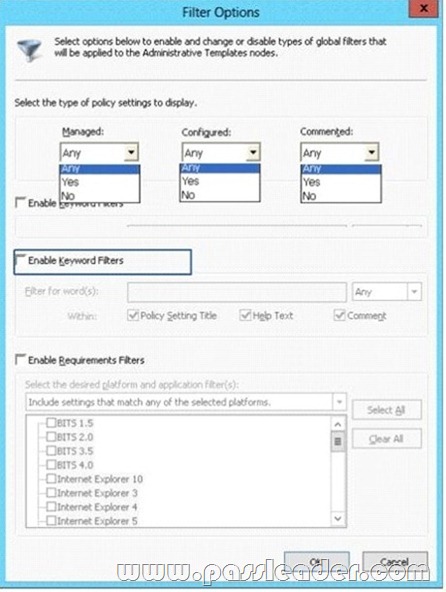
A. Set Managed to: Yes
B. Set Managed to: No
C. Set Managed to: Any
D. Set Configured to: Yes
E. Set Configured to: No
F. Set Configured to: Any
G. Set Commented to: Yes
H. Set Commented to: No
I. Set Commented to: Any
Answer: ADG
QUESTION 300
Your network contains an Active Directory domain named adatum.com. The domain contains five servers. The servers are configured as shown in the following table.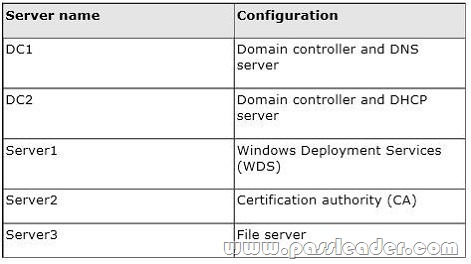
All desktop computers in adatum.com run Windows 8 and are configured to use BitLocker Drive Encryption (BitLocker) on all local disk drives. You need to deploy the Network Unlock feature. The solution must minimize the number of features and server roles installed on the network. To which server should you deploy the feature?
A. Server3
B. Server1
C. DC2
D. Server2
E. DC1
Answer: B
Download Free 70-411 PDF Dumps From Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpfnVfbXEwbmlUa1paemdDc19zQ1JWdVpqU1poRlB2TnktaWlBUFhfQXNJZVU (Explanation For Every Question Is Available!)
PassLeader 70-411 VCE Dumps Screenshots:
Download New 70-411 VCE Dumps From PassLeader: http://www.passleader.com/70-411.html (New Questions Are 100% Available and Wrong Answers Have Been Corrected!!!)